 New version of the Cloud IAP plugin for Remote Desktop released
New version of the Cloud IAP plugin for Remote Desktop released
A few days ago, I released version 1.1.22 of the Cloud IAP plugin for Remote Desktop on Github.
The three main new features in this release are:
- A managed implementation of Cloud IAP TCP tunneling
- OAuth-based authorization.
- Support for custom GCP session lengths.
Managed implementation of IAP TCP tunneling
Previous versions of the plugin relied on gcloud to establish
Cloud IAP TCP tunnels
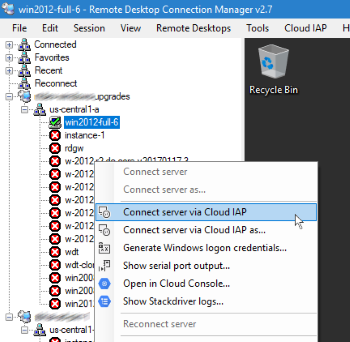
When you selected Connect server via Cloud IAP in the menu, the plugin
spawned a gcloud compute start-iap-tunnel process in the background.
Relying on gcloud to establish Cloud IAP tunnels has a few disadvantages:
- Launching a
gcloudprocess takes several seconds. This causes a noticable delay when trying to connect to a VM instance. - Each VM you connect to requires a separate
gcloudinstance as each instance can only manage a single tunnel. Althoughgcloudis not overly resource-hungry by today’s standards, the memory footprint quickly adds up if you connect to multiple instances:
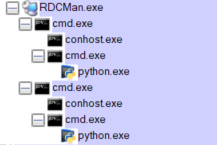
Example of running RDCMan with two active tunnels managed by gcloud
The new version of the plugin does away with this overhead by using a managed
implementation of Cloud IAP tunneling by default. That is, the plugin can now
establish tunnels without having to engage gcloud at all. Not having to spawn gcloud
processes translates into a substantially faster connection time and lower
memory consumption.
The one caveat is that the managed implementation requires at least Windows 8 or Windows Server 2012. To support previous versions of Windows, the plugin therefore allows you to switch back to using gcloud-based tunneling by setting Tunneling implementation to Gcloud in the settings.
OAuth
Because the plugin relied so heavily on gcloud before, it did not make sense for it to implement
its own authentication, so the plugin used your local gcloud credentials
to connect and authenticate to GCP.
Unless you switch back to using gcloud-based tunneling, having the Cloud SDK installed
is now optional. As a result, the plugin also does not require local gcloud credentials
anymore. Instead, it will ask you for your consent to access your GCP projects by using OAuth.

As with any other OAuth-based application, you can check and revoke your consent at any time in your Google Account settings.
Custom GCP session lengths
Recently, GCP introduced the ability to
control the session length for Cloud Console and gcloud sessions.
Although the setting’s name suggests it only applies to the Cloud Console and gcloud,
it really affects all clients that interact with GCP APIs – including the Cloud IAP plugin.
If you specify a custom session length and your session expires, the plugin will now properly prompt you to re-authenticate.
Other changes
A few notable other changes include:
- Generating Windows credentials is now much faster. Again, this is a result of not relying on
gcloudanymore. Instead, the plugin now programmatically creates passwords. - Loading instances is much faster too, thanks to using a different API.
You can download version 1.1.22 on GitHub.