Keeping track of SSH keys using IAP Desktop 2.26
Keeping track of SSH keys using IAP Desktop 2.26
When we allow users to use SSH to connect to Linux VMs on Google Cloud, we need to keep track of their public keys, and which VMs they have access to. That can be easier said than done.
Google Cloud lets us choose between two ways of managing SSH keys for Linux VMs. The classic (and default) way is to use metadata-based keys, where we upload SSH keys to instance or project metadata.
Metadata-based keys are easy to use and understand, but they’re also risky. In fact, metadata-based SSH keys have some of the same problems and risks as service account keys:
- Their lifecycle is disconnected from user accounts: If a user Bob uploads his public key to metadata and subsequently leaves the organization, his key isn’t removed or disabled automatically. The key continues to work until somebody removes it.
- Their identity is disconnected from user accounts: Although the metadata contains a username and email address for each SSH key, this information can’t be relied on – it’s essentially free-text.
- They proliferate: As users access different VMs across multiple projects, they leave more and more copies of their SSH keys in different places of metadata.
The second way to manage SSH keys is OS Login. Instead of associating SSH keys with VMs or projects, OS Login attaches the SSH key to the user account of its owner. That has some important consequences:
- The key’s lifecycle is tied to that of the user account. If we suspend or delete a user account in Cloud Identity or Workspace, we automatically disable the user’s SSH keys.
- There is now a link between the user account and the key, which means we can use IAM to decide which VM a user should be allowed to access.
Given the benefits of OS Login, it’s a good idea to enforce the use of OS Login across all our VMs and projects. But maybe we haven’t done that yet, or maybe we’re using a Linux distribution that doesn’t support OS Login. In these cases, we still have to deal with metadata-based keys.
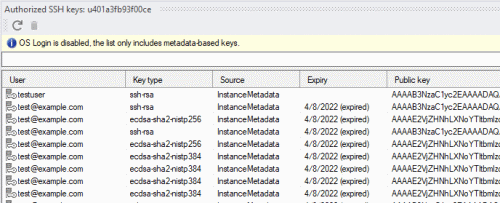
Authorized SSH keys window
IAP Desktop 2.26 now includes a new Authorized SSH keys tool window that makes managing SSH keys a little easier. For each VM or project, the tool window lets us see:
- whether OS Login is enabled or not.
- which metadata-based keys effectively apply to the VM, taking both project-level and instance-level keys into account, and honoring the Block project SSH keys setting.
- which keys have already expired
And if we spot a key that shouldn’t be there, we can delete it straight from within the application.
Other new features
IAP Desktop 2.26 includes some other new features, including:
- Issue reporting: If you don’t have a GitHub account, you can now report issues and feedback on issuetracker.google.com.
- Browser selection: The sign-in screen now lets you choose which browser to use for signing in.
You can find the source code and all releases of IAP Desktop on the project’s GitHub page.