Using ECDSA keys for SSH public key authentication in IAP Desktop 2.23
Using ECDSA keys for SSH public key authentication in IAP Desktop 2.23
By default, IAP Desktop uses the rsa-ssh public key signature algorithm when authenticating
to a Linux VM. rsa-ssh is ubiquitous and still commonly used – but it still relies on SHA1,
which led the OpenSSH team to deprecate it a while ago:
It is now possible to perform chosen-prefix attacks against the SHA-1 hash algorithm for less than USD$50K. For this reason, we will be disabling the "ssh-rsa" public key signature algorithm that depends on SHA-1 by default in a near-future release.
The successors to rsa-ssh are rsa-sha2-512 and rsa-sha2-256. These
algorithms still use an RSA key pair, but use the more modern SHA2 hashing algorithm. Transitioning
from rsa-ssh to rsa-sha2-512 or rsa-sha2-256 is typically straightforward as we can continue
to use the same RSA key.
But not all SSH clients and libraries support rsa-sha2-512 and rsa-sha2-256 yet. One of the
libraries that still lacks support is libssh2,
which is the library IAP Desktop relies on. This has started to become an issue for some IAP
Desktop users who have configured their VMs to reject rsa-ssh – to meet FIPS compliance
requirements, or simply to raise the security bar.
Adding ECDSA support
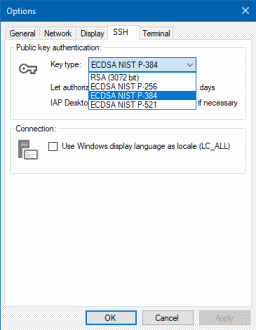
IAP Desktop 2.23 now provides a solution to this issue by letting you switch from RSA to ECDSA encryption. You can now choose the type of key to use in the Options dialog:
Regardless which option you choose, IAP Desktop automatically creates a key using CryptoNG and stores it in the Microsoft Software Key Storage Provider. If you’re curious, you can list the SSH keys created by IAP Desktop by running the following command:
certutil -csp "Microsoft Software Key Storage Provider" -key -user | findstr IAPDESKTOP_
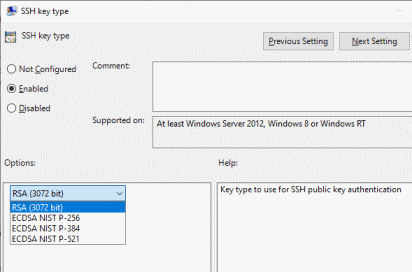
In an enterprise environment, you can go one step further and configure a group policy setting to force IAP Desktop to always use a certain key type and signature algorithm:
A note on EdDSA/Ed25519
Now that IAP Desktop supports ECDSA, you might be wondering whether support for EdDSA/Ed25519 will follow soon. Unfortunately, that’s unlikely: While libssh2 supports Ed25519, CryptoNG doesn’t. And because IAP Desktop relies on CryptoNG for key storage, that means Ed25519 support won’t come anytime soon, or at least not before Windows adds support for it.
You can find the source code and all releases of IAP Desktop on the project’s GitHub page.